Below are the OSINT writeups of all the challenges that were being asked in the VishwaCTF’22, organised by Cyber cell VIIT, Pune.
Caught Very Easily
- The name of the challenge is a hint intself saying CVE(common vulnerabilities and exposures). Also the flag format given (EDBID_Date) is saying that we have to find the ExploitDB id of some attack.
- Seeing the question again now also tells us that “JAILBREAK” is an important keyword. Reasearching on internet tells us that it is a type of malware to gain access to mobile devices.
- Carefully searching for “Ahmed Masoor’s” on internet with “Jailbrake” we understand that this is a true story which lead to the discovery of “Pegasus” spyware.
- Now we understand that we have to find the EDBID and date of the vulnerabilities that were used by the Pegasus spyware. In ExploitDB we can find vulnerabilities to use in softwares like metasploit. To search ExploitDB we have to know what vulnerabilities pegasus used.
- We search internet for the details of pegasus and find Vulnerabilities used were: CVE-2016-4655: Information leak in kernel – A kernel base mapping vulnerability that leaks information to the attacker allowing them to calculate the kernel’s location in memory. CVE-2016-4656: Kernel memory corruption leads to jailbreak – 32 and 64 bit iOS kernel-level vulnerabilities that allow the attacker to secretly jailbreak the device and install surveillance software – details in reference.[66] CVE-2016-4657: Memory corruption in the webkit – A vulnerability in the Safari WebKit that allows the attacker to compromise the device when the user clicks on a link.
- We find one entry in ExploitDB for the search “2016-4655″/”2016-4656″/”2016-4657” and on clicking we find EDB-ID : 44836 Date : 2018-06-05
Money Money Money
Heading: Money money money
Writeup:
- The zip file money.zip has a password so we will have to find the password somehow
- We start with the richies.jpeg file, it is a message in numbers which will have to be converted into text. After researching a bit we get it is a sms phone tap code cipher.
- After decoding it using online tool SMS Phone Tap Code Cipher (Multitap Mode) – Online Decoder, Translator (dcode.fr) we get : IN THE LAST YEAR I INVESTED IN HUNDRED DOGECOIN GOLD AND GOT HUGE PROFITS. HAVE A LOOK AT SOME OF MY TRANSACTIONS. IF YOU ARE STUCK, YOU HAVE EVERYTHING YOU NEED LOOK CLOSELY
- Now we can understand we have to find a transaction of 100 dogecoin gold somewhere which can lead us further but where to find these transaction? The message says everything is given to us.
- So we check the richies.jpeg file and strings it we see there is a index.jpeg hidden in it. We unzip richies.jpeg to get this image
- After reverse searching this image on google images we get that this is a logo for the site Ethereum (ETH) Blockchain Explorer (etherscan.io)
- Now we have to look for the correct transaction so in the search bar we put dogecoin gold as search filter and see this:


- Here we have 3 transactions in last year with 100 dogecoin gold transferred we check each transaction one by one. In the last transaction we get this in the comments section:
- Here we can see author is trying to hint that the password to the zip file we need is the name of 2 people owning a cryptocurrency company.
- By this chat we can understand that this company as in some leaks offshore and that it is based in Barbados. So we search on google offshore leaks and find this site: ICIJ Offshore Leaks Database
- Here we can search for a company in the entire offshore leaks database. We know that the company we are looking for is a cryptocurrency company so we search it and find one company that matches our criteria
- Inside this we get the name of two directors
- So the 2 people are Esper and Louis so we try both combinations i.e ESPER_LOUIS and LOUIS_ESPER. The second one is the correct one and we get the image money.jpeg from the zip file.
- The image is nothing special but after some stegnography, we use steghide to extract any possible data and get the file flag.txt.
- The flag is VishwaCTF{d0nt_l00k_@_my_m0n3y$}
No Way Home
1)Now here with the given image everything seems to be blur. But have you seen the reflection on the mirrors of that building, there are some alphabets?
2)If you look carefully there are 5 letters “S”, a light reflection of “E”, “C”, “A”, “P”.
3)Now if you search “SECAP” on the maps, and look for 3d street maps of all of them you can narrow down your search to “ECUADOR”
4)Just zoom the map you’ve got and that’s it, you have the street name!


PlatyPus Perry
- We are given with an audio file, we you listen clearly it doesn’t look like something encoded, its just a normal audio with changed pitch, just reverse it and you will hear English alphabets, write down them, and read them reverse, you’ll get a message “our bug guy David Bombal might tell u something which suits ur brain”.
- Now looking at the file name “hire-me” gives you hint of LinkedIn, if you search David Bomabal on LinkedIn search for a “bug bounty” post you’ll see a comment written in “brainfuck”.

- When you decode the brainfuck you’ll get a link to mediafire file sharing platform.

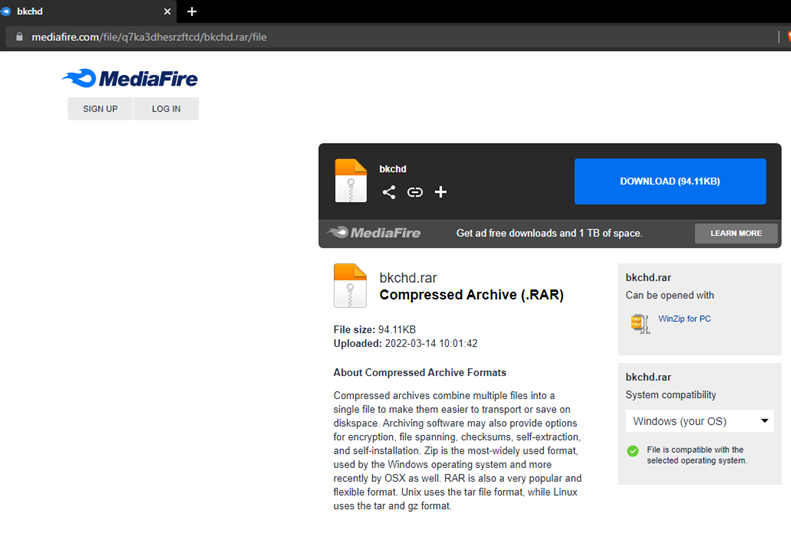
- Now download that file it’s password protected, now crack the password using “johntheRipper” password is: idgaf
- Now you’ll see an image of a guy, just unhide the message in it using online steganography decoder. It has a message “this guy’s pet love them fries, that’s your final pin”.

- Now here we have two hints that his pet with fries and “final pin” hints about Pinterest.
- First, we need to find this man, by doing reverse image search on Pinterest.

- Here we found that he’s a guy “Polishviking” on Instagram, if we search his account and scroll deep in search of a dog pic, you’ll see his post, tagged with the account of his dog!

- Open his dog’s account and there it is i.e. Name of the Dog = flag.
Rocket Raccoon
Rocket Raccoon:Who is ‘racckoonn’ exactly? Intel has that their owner has leaked some private information.
The question starts with giving us a name ‘racckoonn’ and since its an OSINT question,my first instinct would be to search up for accounts on various social media platforms
After some research you would come across an account on instagram with the same name https://www.instagram.com/racckoonn
Looking through the posts , We find a link to a channel that is the owner’s account.
Check out my mum’s new YouTube channel! https://www.youtube.com/channel/UCDurVPcUypifNkJVrHxJ3vQ

The username is :JohnsonM3llisa and no other information is listed anywhere on this account
Let’s try to use this username on other platforms to see if they give us some result.One can also use Sherlock(an osint tool) to check multiple platforms for accounts with the username.
Twitter.com/JohnsonM3llisa gives us some result
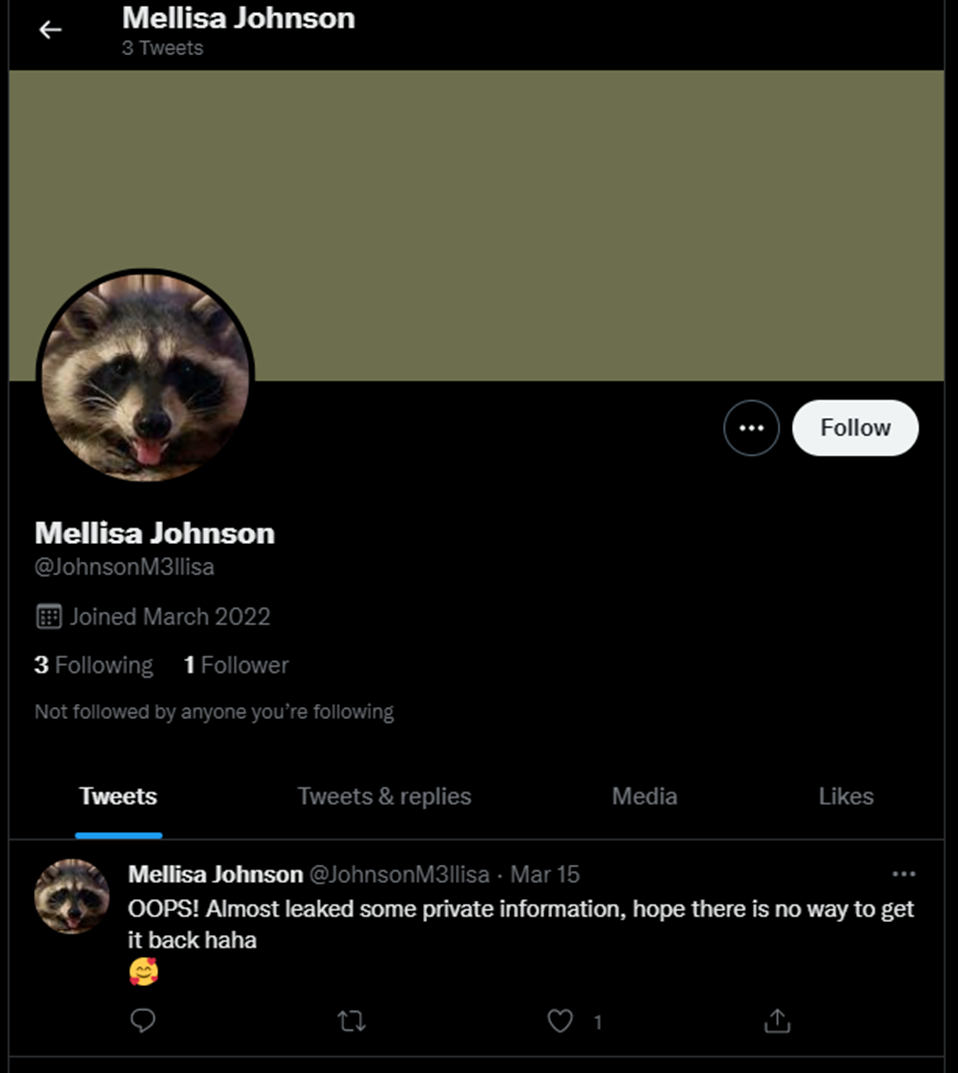
The account is all about the owner’s pet and we see some tweets.The latest tweet says OOPS! Almost leaked some private information, hope there is no way to get it back haha.
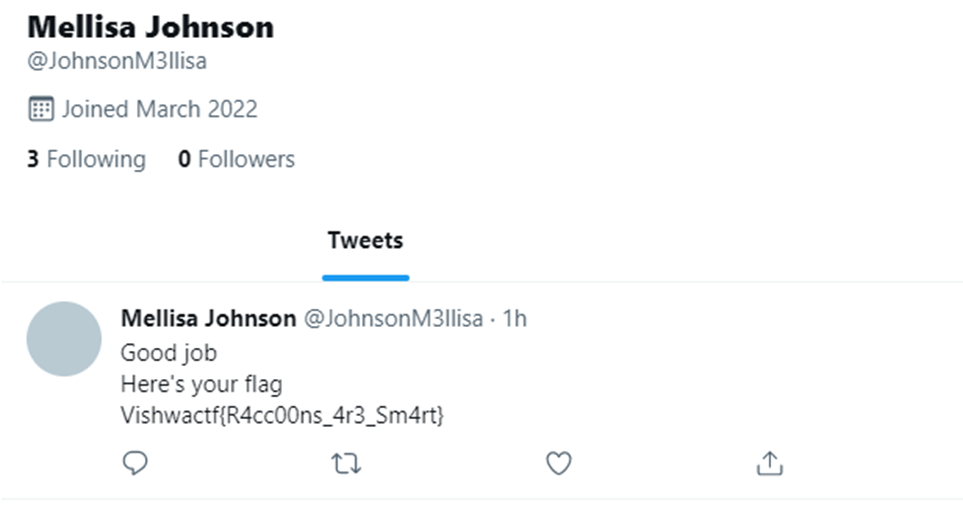
Is there someway to get deleted tweets back? There is! The hint in the tweet was “way to get it back” Using wayback machine,we try to recover any deleted tweets March 15,2022 seems to have some snapshots saved so we go ahead and take a look
The tweet reads “Good job Here’s your flag Vishwactf{R4cc00ns_4r3_Sm4rt}”,and that is the end of this challenge.
The Library
The challenge description states that “Send a ‘hello’ to “The Librarian” from the bot list on the Discord server, and he shall guide you further.”
There are a few images attached for troubleshooting, which are not associated with the challenge directly.
On messaging The Librarian, we are started off with –

The first line indicates that we need to look out for books.
On Googling the quote ‘Very few of us are what we seem.’, we get the name of the book and the author, “The Man in the Mist” by Agatha Christie. Exploring the wiki pages of the book gives us the required information.

Searching directly for “Tommy is to call on Miss Glen at what time?” also leads us to the Partners in Crime short story collection, where the Wikipedia page contains the time directly.
Entering this in the specified format takes us to the next step –

We have the name of the book in the statement itself. So searching for The Son of Neptune seer leads us to Phineus (multiple sources for this – the Wikipedia page, the Wiki page, summaries). From the next sentence we look around for Phineus in mythology – searching for Phineus seer mythology leads us to multiple pages (Wikipedia, greekmythology sites) which contain the required information – The Golden Fleece (Golden Fleece is an accepted submission as well, no case sensitivity)

Moving on to the next part, we have –

Searching for ‘The year without a summer, a vacation, and a classic was created.’, gives us the year as 1816, and several articles pointing towards the intended book “Frankenstein” (some articles for your reference – 1, 2, 3, 4).
The next line is confirmed from the Wikipedia page for the book –

From this we need to enter the university of the creator, which is University of Ingolstadt.
For the next part we have –
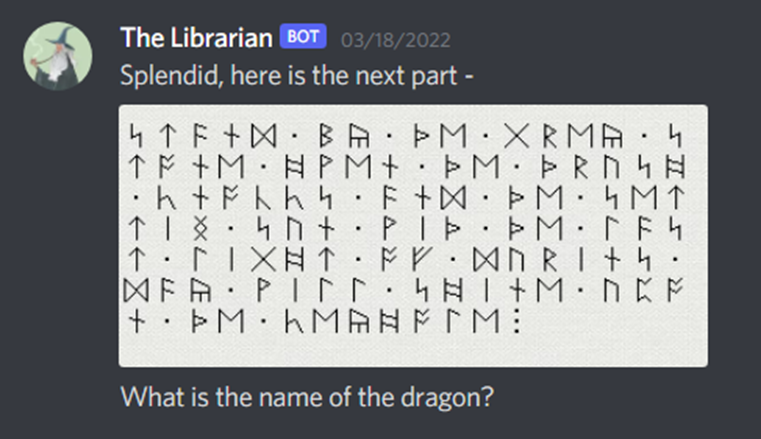
Using Google Lens to dig around a bit, we understand that the given runes are Anglo Saxon. Translating them, we get

Searching for this quote gives us the name of the book for this step “The Hobbit”. From this, the name of the dragon is a Google search away – “Smaug”.
For the final part of the challenge, we have –

For this step, there was a direct reference to the book name with the capitalized letters, but not the only one, just to make life a bit easier. If this was missed, the line “These Symbols might make you feel pretty Lost, but not as much as a severed hand right in the ‘place in the image’ served as the book reference.
Reverse Googling the image reveals that it is of the US Capitol. So searching for the phrase gives us the name of the book “The Lost Symbol” by Dan Brown.
The last step involves cryptography, however the cipher used is completely from the book, so simply Googling for The Lost Symbol cipher gives us the method which was used in the book. The steps which are required are pigpen followed by Duhrer’s magic square. Some sources for this are – 1, 2, 3.
The step where most people were stuck was due to just going with Pigpen, which was pretty easy to identify, being a common cipher. However, this step was in accordance with the theme of the question, hence the implementation of all the steps was needed to get the right answer.
Decrypting the pigpen gives us ‘nisytetprisnufo’, followed by the Duhrer square, which gives us ‘osintisprettyfun’.
Entering this gives us the flag –
Not so Tough!
- Given with the pic, what you see is a strange pic on the left corner with some colours, it has some encoded message.
- Its actually a HexHue code, decoding it you’ll get – “stokfredrik”

- If you search about him he’s a bug bounty hunter, now looking at the name of the given picture as “picoftheday” you get a hint of Instagram.
- When you go to his Instagram, his second post of his studio has a “DNA codon” in the comments, decode it to English (case sensitive), you’ll get a pastebin link.

- If you open it you’ll see a random code which has “flag info: “ and some “Chinese looking text” in front of it.
- Also at the end of the code, its written as “//code contains 65536 lines”, that’s actually a hint for the Chinese text, which is not Chinese. Its actually “base 65536”.
- Decode it using base 65536, and hola you get the flag!

Get the latest tech news and updates, ethical hacking tutorials and cybersecurity tips and tricks. Check out MeuSec for more.
Sometimes we include links to online retail stores and/or online campaigns. If you click on one and make a purchase we may receive a small commission.


Comments: