Have you ever called a friend, or received an SMS, and wondered how does it know where to go? If the answer’s yes, you will have your curiosity cleared (and learn a cool new hacking technique along the way) What is SS7? SS7, or Signalling System No. 7, is an international standard network signaling protocol that allows […]
The right way to send a secret message to anyone, understanding the basics of 3 pass protocol
Major giveaway of a certied penetration testing or hacker training worth Rs.30,000 or $410 on the occasion of our 1 year anniversary. Particiapte now!!
This post is a walkthrough of the PickleRick which is a Rick and Morty themed Tryhackme room. The goal is to find three hidden flags.
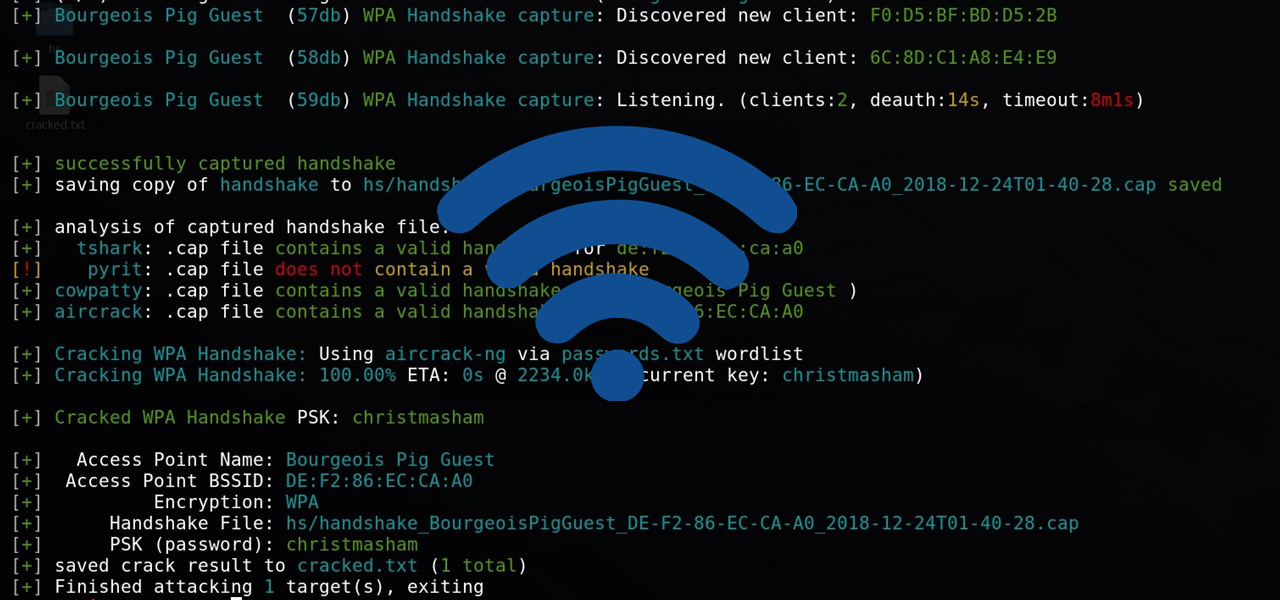
The most basic steps and explanation to crack any WPA, WPA2-PSK networks using Airmon-Ng.
The second phase of ethical hacking and penetration testing involves two terms that are Vulnerability Scanning and Enumeration. Scanning involves taking the knowledge discovered during reconnaissance and using it to look at the network
Information gathering isn’t just a phase of security testing; it’s an art that each penetration tester and hacker should master. Let’s dive deeper into it.
The 5 Phases of Hacking are: Reconnaissance, Scanning, Gaining Access(Exploitation), Maintaining Access/Persistence and Clearing Tracks.
In the information security (InfoSec) community, “CIA” has nothing to try to to with a particular well-recognized US intelligence. These three letters stand for Confidentiality, Integrity, and Availability, also known as the CIA Triad. Together these principles are the foundation of any organization’s information security.
There’s no fixed way to start hacking, and you need not be of a computer science background to learn this. But there are some basic knowledge and things you need to know in order to become one.
Here are 3 main things every Beginner Hacker should know about. These tips will get you started and are very important.