Below are the Cryptography writeups of all the challenges that were being asked in the VishwaCTF'22, organised by Cyber cell VIIT, Pune.
John the Rocker
Step 1: Convert the given id_rsa file to the hash file. (use the ssh2john.py for the same) Command: pyhton3 ssh2john.py id_rsa.idrsa.docx > hash
Step 2: Use john the ripper to find the flag from the hash file. (Use rockyou.txt as a wordlist) Command: john -w=(Path of rockyou.txt) hash
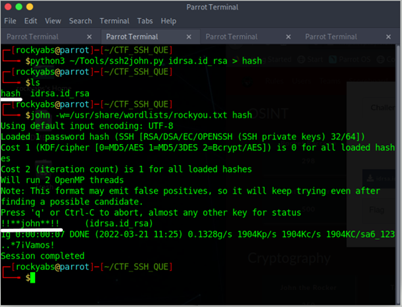
Flag: VishwaCTF{!!john!!}
Jumble Bumble
Flag: VishwaCTF{c4yp70gr2phy_1s_n07_e25y}
The ciphertext is short and e=4 is also small. Brute Forcing c + k *n for each positive integer k. Getting the perfect root which is just the plaintext we can find the flag.
from Crypto.Util.number import inverse, long_to_bytes
from sympy import integer_nthroot
file = open("output.txt", "rb")
while True:
n = int(file.readline().strip())
c = int(file.readline().strip())
dis = file.readline()
while True:
ans = integer_nthroot(c, 4)
if ans[1]:
m = ans[0]
break
plaintext = long_to_bytes(m).decode()
print(plaintext)
Musical Notes
In the question, we have been given an Image of Musical notes. On searching, we get to know it is Acéré Cipher. Also, the hint given in this question states that it is Acéré Cipher. Hint: All Chores Encloses Rare Encryption cipher. Joining the first letter of all works except cipher gives us the idea that it is the Acéré cipher. Decoding an image with Acéré Cipher give a random string.
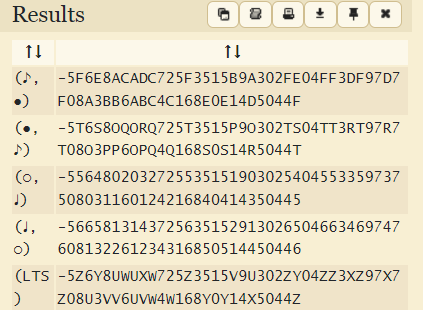
Taking the first one as its default. Decoded String becomes 5F6E8ACADC725F3515B9A302FE04FF3DF97D7F08A3BB6ABC4C168E0E14D5044F Now as Stated in Question Description, there was SEA of images. In this SEA is highlighted, cracking it we can get to know it’s something related to AES also there’s a string given in the question, i.e., listentocoolsong. It is visible that length of this string is 16 which makes sense for AES Decryption. Hence doing Decryption using AES we can get Flag.

Flag: vishwaCTF{mus1c4l_c1ph3r_1n_4ct10n}
Tallest header
We have been given a file named file.extension, whose file type is not visible in file command in Linux. So, analyzing the file using Hexedit we can get a hint that file is JPG image.
Header of this JPG image is changed; hence image was not recognized as JPG. Changing the starting HEX to the original format of JPG which is FF D8 FF we can make file detectable as Image.

But after opening Image file we can see that there’s nothing but Tallest Header Goal by Ronaldo. Now if someone thought that image will get you to Flag, they are fallen for Rabbit Hole. There something behind this image hidden using Steganography, which zip file and can be extracted by using command unzip on terminal.

From that zip we got two new files, i.e., encrypt.py and info.txt. encrypt.py contain a python script for encryption of Flag using simple Permutation Cipher Algorithm. We must write decrypt function for the same and pass parameters from info.txt in decrypt function. In decryption function we just must inverse the key and pass inversed key and ciphertext to encrypt function to decrypt the original Flag. decrypt.py def inverse_key(key): inverse = [] for position in range(min(key),max(key)+1,1): inverse.append(key.index(position)+1) return inverse def decrypt(key, ciphertext): return encrypt(inverse_key(key), ciphertext) print(decrypt(key, ciphertext)
after decrypting we get a flag as output vishwaCTF{tr1cky_h34d3r_w1th_p3rmu7at10n}
Wierd Programmer
Weird Programmer Flag : vishwaCTF{1T_1S_W31RD_N0T_T0_B3_W31RD} Question Description: I bet my friend who is a terrible poet and a really weird programmer that i can solve any encryption he makes in less than 3 tries but i may have underestimated him. Can you help me win this bet?
attachment : poem.txt , weird programmer.txt
Poem.txt contents : When you have broken the glass and stepped into the eighth circle of hell, you will find yourself under the pollux's spell and after that you will be able to tell, All's well that end's well
weird programmer.txt contents {M[m(o)O!"'&BA@?><543Wxwvutsrqponmlkjihgfe#zyx}|{zyrwp6WVUTSRQglejihgfe^$#DCBA@?>=<RW VUTMRQJIm0/.-,+*)('&%$#"!}|{zyxwvutsrqponmlkjihgfedcba_^]\[ZYuWmrqpinmlkjc )gf_d]#DCBA@?UZYXWPUTSRKoONGLKDh+*)('&%$@?8=<5:9810Tut210/.-,+k#Ghgfedcba^ ][ZYXWmlkjonmlkjib(fHdcb[!X]VzZSRvVOsMLQJONMFEiIHAFE>bB;:?87[|{zyxwvutsrqp onmlk)i'&%$#"!~}v<][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('=BA :?>=<;:92V05.3,10)Mnmlkjihgfedcba_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876 543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba^][ZYXWVUTSRQPONMLKJIH GFEDCBA@?>=<;:9876543210/.-,+)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba_^]\[Z YXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponml kjihgfedcba_^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+)('&%$#"!~ }|{zyxwvutsrqponmlkjihgfedcba_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:98765432 10/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba^][ZYXWVUTSRQPONMLKJIHGFED CBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba_^]\[ZYXWV UTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjih gfedcba^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+)('&%$#"!~}|{z yxwvutsrqponmlkjihgfedcba_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/. -,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba_^][ZYXWVUTSRQPONMLKJIHGFEDCBA@ ?>=<;:9876543210/.-,+)('&%$#"!}|{zyxwvutsrqponmlkjihgfedcba}|{zyxwv utsrqponmlkjihgfedcba_^]\[ZYXWVUTSR QPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfed cba_^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+* )('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=< ;:9876543210/.-,+)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba_^]\[ZYXWVUTSRQPON MLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba _^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?[ZSXWVUTSRQPONMFjJCHA@d>CBA@?8}|{zyxwvutsr qponmlkji!&%$#"!w|u;yxqputsrk1oQmle+iha'_dcb[ZA@?>=<;:9876543210/.-,+)('= <A@?>=<543W7654t210)Mnmlkjihgfedcba_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:98 76543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba^][ZYXWVUTSRQPONMLKJ IHGFEDCBA@?>=<;:9876543210/.-,+)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba_^]\ [ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqpon mlkjihgfedcba_^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+)('&%$#" !}|{zyxwvutsrqponmlkjihgfedcba}|{zyxwvutsrqponmlkjihgfedcba_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:987654 3210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba_^][ZYXWVUTSRQPONMLKJIHGF EDCBA@?>=<;:9876543210/.-,+*)('&%$#"!_^]\[ZYX WVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkj ihgfedcba^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}| {zyxwvutsrqponmlkjihgfedcba_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210 /.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba^][ZYXWVUTSRQPONMLKJIHGFEDCB A@?>=<;:9876543210/.-,+)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba_^]\[ZYXWVUT SRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgf edcba_^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+)('&%$#"!}|{zyx wvutsrqponmlkjihgfedcba}|{zyxwvutsrqponmlkjihgfedcba_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-, +*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba_^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?> =<;:9876543210/.-,+*)('&%$#"!_^]\[ZYXWVUTSRQP ONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcb a^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?[ZSXWVUTSRQPONMFjJCg*)('&%$#"!}|{zyxwvut srq/.-,+k)"'&}|B"!|u;\[ZYXWVUTSRQPONMLKgfe^cbaY^]Vz=<;:9876543210/.-,+)( '&%$#"!}|{zyxwvutsrqponmlkjihgf|#"y}|{zyxwp6WVUTSRQmlkjibge^$EaY}][Z<XW POs6543210/.-,+)('&%$:?8=6;:9870Tu-2+*NMnmlkjih&%$#"!~}|u;[ZYXWVUTSRQPONML KJIHdcbaY^]V[TxXWVUTMRQJnHl/.-,+*)('&%$#"!~}|{3816543210)Mnm+*#(!&%$#z@x}v< tyr8YXWVUTSRQPONMLKJIHGFEa^]V[ZSXQuUTSRQ3INGkKJIHG@?c&%$#"!}|{zyxwvutsr0/ .-,+)(h&}C#"bx>|{tyrqvun4rqjonmle+LKJIHGFEDCBA@?>=<;:9876543210/.-,+)('&%$ #"!}|{zyxwvutsrqponmlkjihgfedcba|{zyxwvunslk1Rnmlkjiha'HGFEDCBA@?>=<;:9876 543210/.-,+*)('&%$#"!~}|{zyxwvutsrqpo-,l*)('~%|#"y?^][ZYXWVUTSRQPONMLKJIH GcEaY^]V[TSRv9876543210/.-,+*)('=B;@?>=<;:3W7w543,Pqponml$#(!~%$#"!x>_{zyxq 7XWVUTSingledihgf_%c\aZ~^]?UZYXWPtTMLp3INGk.-,+*)E'=B;:?>=<5Yz876543,Pqponml k)('&%$#"!x>_^]yxwvutsrk1RQPONMLKgfedcbaYXW{[ZYXWPUTMqQJImMFKJIHAe('=B;@?>= <;4XWV0543210)M-&+*)"Fgfedcba_^]\[ZYXWVrqSinglkjiha'HGFEDCBA@?>=<;:98765432 10/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba^][ZYutmrkponmledc)afe^$E[ Z_^]VzTYRWVONrLQPONGLKDh+*)('&<A@?>=<;:92VC"(_o)o.?]}
Detailed Solution : Hints to identify from the poem
- broken the glass
- eight circle of hell
- Pollux’s spell
Step 1 : Run Glass code On searching on google you find that Glass is an esolang for which you can find a lot of information online. Given below is the wikipedia page for Glass Language : https://esolangs.org/wiki/Glass If you see in the examples section you will see the code for the “Hello World” program in glass on observing this you will see that just the words Hello World have been replaced with another ciphertext . Just remove this syntax for glass and you have successfully broken the glass. you get the ciphertext as : Ciphertext = '&BA@?><543Wxwvutsrqponmlkjihgfe#zyx}|{zyrwp6WVUTSRQglejihgfe^$#DCBA@?>=<RW VUTMRQJIm0/.-,+*)('&%$#"!}|{zyxwvutsrqponmlkjihgfedcba_^]\[ZYuWmrqpinmlkjc )gf_d]#DCBA@?UZYXWPUTSRKoONGLKDh+*)('&%$@?8=<5:9810Tut210/.-,+k#Ghgfedcba^ ][ZYXWmlkjonmlkjib(fHdcb[!X]VzZSRvVOsMLQJONMFEiIHAFE>bB;:?87[|{zyxwvutsrqp onmlk)i'&%$#"!~}v<][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('=BA :?>=<;:92V05.3,10)Mnmlkjihgfedcba_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876 543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba^][ZYXWVUTSRQPONMLKJIH GFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba_^]\[Z YXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponml kjihgfedcba^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+)('&%$#"!~ }|{zyxwvutsrqponmlkjihgfedcba_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:98765432 10/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba_^][ZYXWVUTSRQPONMLKJIHGFED CBA@?>=<;:9876543210/.-,+)('&%$#"!}|{zyxwvutsrqponmlkjihgfedcba}|{z yxwvutsrqponmlkjihgfedcba_^]\[ZYXWV UTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjih gfedcba_^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/. -,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba^][ZYXWVUTSRQPONMLKJIHGFEDCBA@ ?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba_^]\[ZYXWVUTSR QPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfed cba^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+)('&%$#"!~}|{zyxwv utsrqponmlkjihgfedcba_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+* )('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba_^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=< ;:9876543210/.-,+)('&%$#"!}|{zyxwvutsrqponmlkjihgfedcba}|{zyxwvutsrqponmlkjihgfedcba_^]\[ZYXWVUTSRQPON MLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba ^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?[ZSXWVUTSRQPONMFjJCHA@d>CBA@?8}|{zyxwvutsr qponmlkji!&%$#"!w|u;yxqputsrk1oQmle+iha'_dcb[ZA@?>=<;:9876543210/.-,+*)('= <A@?>=<543W7654t210)Mnmlkjihgfedcba_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:98 76543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba^][ZYXWVUTSRQPONMLKJ IHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!_^]\ [ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqpon mlkjihgfedcba^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#" !~}|{zyxwvutsrqponmlkjihgfedcba_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:987654 3210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba^][ZYXWVUTSRQPONMLKJIHGF EDCBA@?>=<;:9876543210/.-,+)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba_^]\[ZYX WVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkj ihgfedcba_^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+)('&%$#"!}| {zyxwvutsrqponmlkjihgfedcba}|{zyxwvutsrqponmlkjihgfedcba_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210 /.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba_^][ZYXWVUTSRQPONMLKJIHGFEDCB A@?>=<;:9876543210/.-,+*)('&%$#"!_^]\[ZYXWVUT SRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgf edcba^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyx wvutsrqponmlkjihgfedcba_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-, +*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?> =<;:9876543210/.-,+)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba_^]\[ZYXWVUTSRQP ONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcb a_^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?[ZSXWVUTSRQPONMFjJCg)('&%$#"!}|{zyxwvut srq/.-,+k)"'&}|B"!|u;\[ZYXWVUTSRQPONMLKgfe^cbaY^]Vz=<;:9876543210/.-,+)( '&%$#"!}|{zyxwvutsrqponmlkjihgf|#"y}|{zyxwp6WVUTSRQmlkjibge^$EaY}][Z<XW POs6543210/.-,+)('&%$:?8=6;:9870Tu-2+NMnmlkjih&%$#"!}|u;[ZYXWVUTSRQPONML KJIHdcba}|{zyxwvutsr0/ .-,+)(h&}C#"bx>|{tyrqvun4rqjonmle+LKJIHGFEDCBA@?>=<;:9876543210/.-,+)('&%$ #"!~}|{zyxwvutsrqponmlkjihgfedcbaY^]V[TxXWVUTMRQJnHl/.-,+*)('&%$#"!~}|{3816543210)Mnm+*#(!&%$#z@x}v< tyr8YXWVUTSRQPONMLKJIHGFEa_^]V[ZSXQuUTSRQ3INGkKJIHG@?c&%$#"!|{zyxwvunslk1Rnmlkjiha'HGFEDCBA@?>=<;:9876 543210/.-,+*)('&%$#"!~}|{zyxwvutsrqpo-,l*)('~%|#"y?_^][ZYXWVUTSRQPONMLKJIH GcEaY^]V[TSRv9876543210/.-,+*)('=B;@?>=<;:3W7w543,Pqponml$#(!~%$#"!x>_{zyxq 7XWVUTSingledihgf_%c\aZ~^]?UZYXWPtTMLp3INGk.-,+*)E'=B;:?>=<5Yz876543,Pqponml k)('&%$#"!x>_^]yxwvutsrk1RQPONMLKgfedcbaYXW{[ZYXWPUTMqQJImMFKJIHAe('=B;@?>= <;4XWV0543210)M-&+)"Fgfedcba_^]\[ZYXWVrqSinglkjiha'HGFEDCBA@?>=<;:98765432 10/.-,+*)('&%$#"!~}|{zyxwvutsrqponmlkjihgfedcba^][ZYutmrkponmledc)afe^$E[ Z^]VzTYRWVONrLQPONGLKDh+*)('&<A@?>=<;:92VC
Step 2 : Now if you google Eight Circle as hell you get the answer as Malbolge now if you run the malbolge in any malbolge interpreter you get the following cipher text: ciphertext = AR11J65VQOV3ZXSOTWS7FEGJH84C5BDMGOU5Q86N0LBBRJTH4KJLG41WRVTFYELAQATJIPN4LQXFJWUQCCC12MRXITO3
Step 3 : now pollux’s spell suggests that it is a pollux cipher decode it in any online decoder to get the original message as : flag = 1T1SW31RDN0TT0B3W31RD wrap it in flag format to get submission ready flag as : Final flag : vishwaCTF{1T_1S_W31RD_N0T_T0_B3_W31RD}
Wrong Direction
By Extracting the tar file a structure of nested folders can be found. Each folder contains a suspicious file.
The filenames are some encoded string or cyphers of a youtube link to get RickRoll. Inside every file, there are digits containing 0's and 1. Each file contains only one 1 and the others are 0's
If noticed carefully the number of digits inside a file is equal to the number of chars in the file name. Suggesting it has something to do with the file name.
By using a Python script a string can be made using a char from the file name corresponding to the position of 1 in the same file.
Here could be the sample script.
import os
chipher = ""
base = "1"
while True:
names = os.listdir(base)
if len(names)==0:
break
if len(names[0]) <3:
diret = names[0]
fname = names[1]
else:
diret = names[1]
fname = names[0]
name = f"{base}/{fname}"
with open(name, 'r') as file:
text = file.readline()
where = text.find("1")
letter = fname[where]
chipher += letter
base += f"/{diret}"
print(chipher)
By the script we get a string <bZVgG@<j<7XI"$H!b5>?ScS00OunU3IL
Looking at this carefully, the presence of a few chars indicates that the string actually is a base85 encoded string.
By Decoding the string from Base85 the flag can be found.
Get the latest tech news and updates, ethical hacking tutorials and cybersecurity tips and tricks. Check out MeuSec for more.
Sometimes we include links to online retail stores and/or online campaigns. If you click on one and make a purchase we may receive a small commission.



Comments: