So this weekend, I participated in a CTF challenge that was organized by GirlScript Goa. It was among the beginner level CTFs, so I was able to solve all but one problem. Nonetheless, I came in 3rd in this and here is my writeup for the solutions of the challenges that I solved.
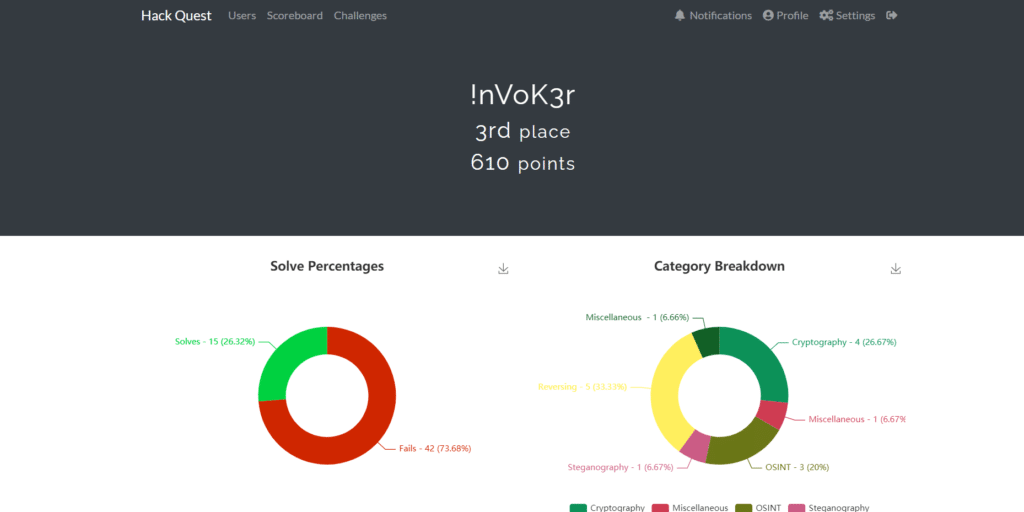
Table of Contents
Miscellaneous Challenges
A Hearty Welcome! (10)
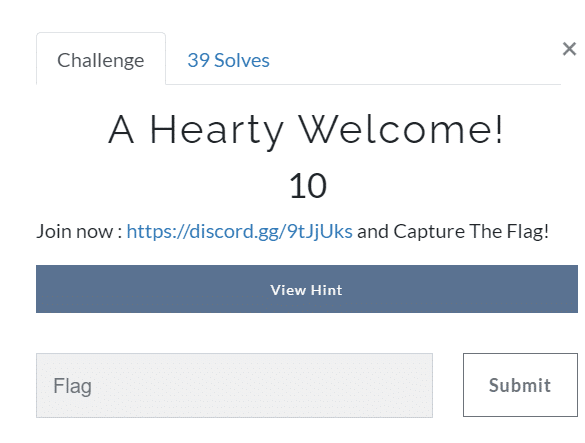
It was a 10 point challenge and the easiest one.
Challenge description –> Now: https://discord.gg/9tJjUks and Capture The Flag!
This one was a complete no brainer as you have to join the discord, and the bot will give you the flag–> heLl0{WelC0me_70_h4X0r_kwe57}.
The Diamond (20)
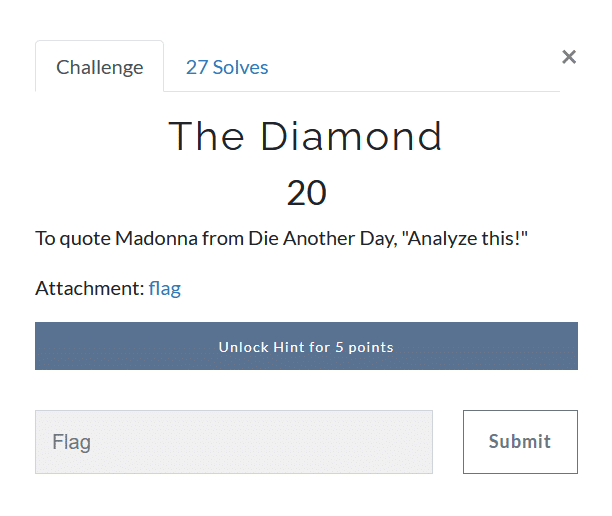
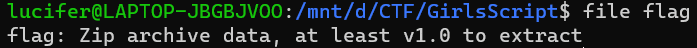
This one was a bit tricky, the flag file has no extension to know how to open it. But just for this purpose, there is a linux command file which tells the file type of a given file. Running this command on the flag, we get the result that it is a ZIP Archive.
After unzipping, we repeat the process and find that it is a bzip2 archive. Repeating the same process over 4-5 times we finally get ASCII text which gives us the flag: gsCTF{0h_l0rd_0f_dec0mpr3ss10n}
Steganography Challenge
Make America Great Again (30)
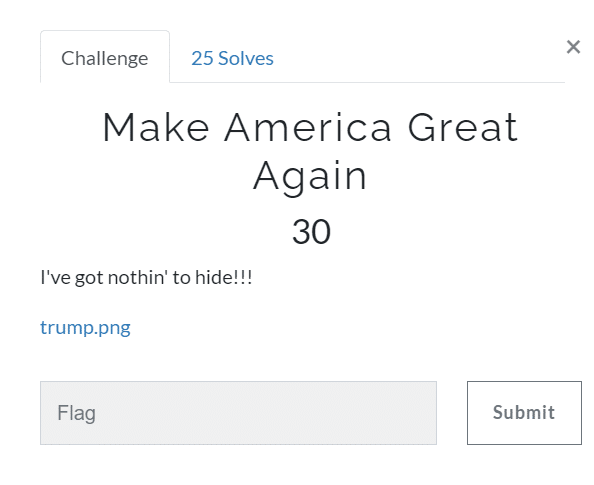

When you see a png image in a steganography challenge, the first thing that pops in mind is the zsteg tool. So, we run the tool in kali, and we got a message.
Ah, you got me there! Here you go:\ngmdzQ1RGe3cxbl90aDNfNHJ0XzBmX3RoM19zdDNnfQ==
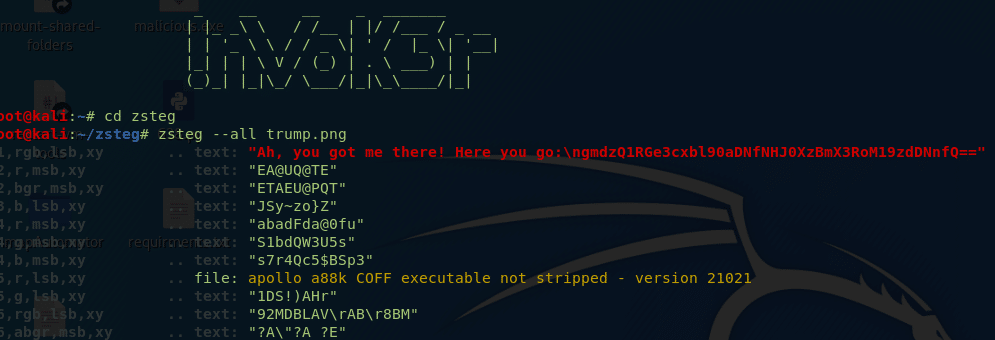
This is a base64 encrypted text after decrypting it using an online decoder we got the flag–> gsCTF{w1n_th3_4rt_0f_th3_st3g}.
OSINT Challenges
The Social Butterfly (50)
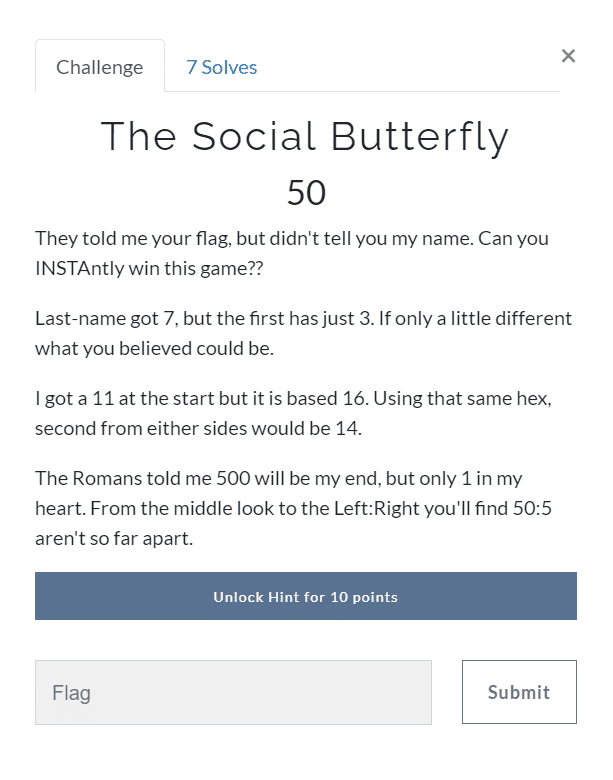
It was one of the trickiest challenges in the CTF. Personally, it took me quite a while to figure out the solution.
Here if we go line by line, the first hint we get here is INSTA.
Which means that the word that we want to decode could be an Instagram username or a hashtag. From the second line, we got to know that there are two words first one is of 3 letters and the later one is of 7.
Now the next statement gives us a hint 11 that is based 16 which means its hexadecimal character, i.e. b and similarly the hex value of 14 is e and e is either side of the word means at the second and the second last position.
The Romans told me 500 would be my end indicates the 500 in roman numeral form, i.e. D is at the end and 1, which indicates I in roman form is in the heart that means the middle, from middle 50(L) and 5(V).
These all words can be decoded from the lines now if we see we got 7 characters and we also know the position as given in the ques.
Now the word becomes belived, and if you read carefully the fourth line indicates a little different what you believed could be.
So the first word could be you 🤔. Let’s see if we get something.
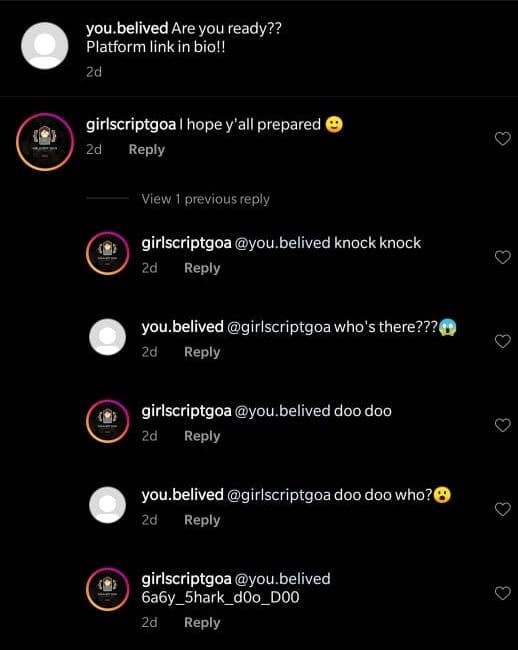
And Voila!!! Got an account on Instagram named @you.belived and if we check the comments on the most recent picture we get the flag 😉.
Where am I? (50)
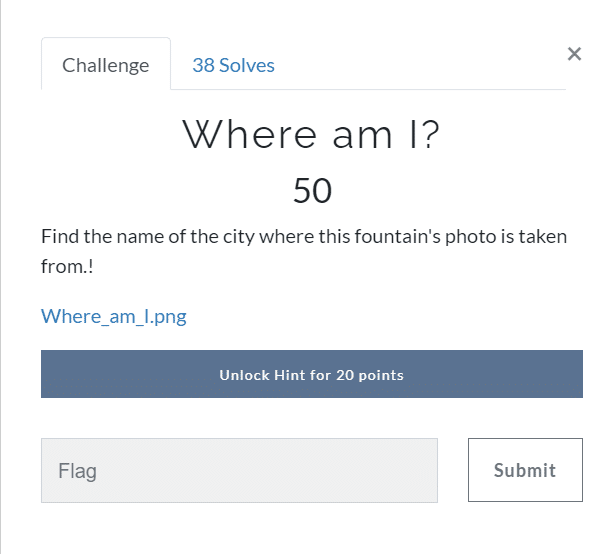

As you can see we got an image from the challenge description
And I did a reverse search on google, and after some crawling, I found the same image on a Bulgarian blog.
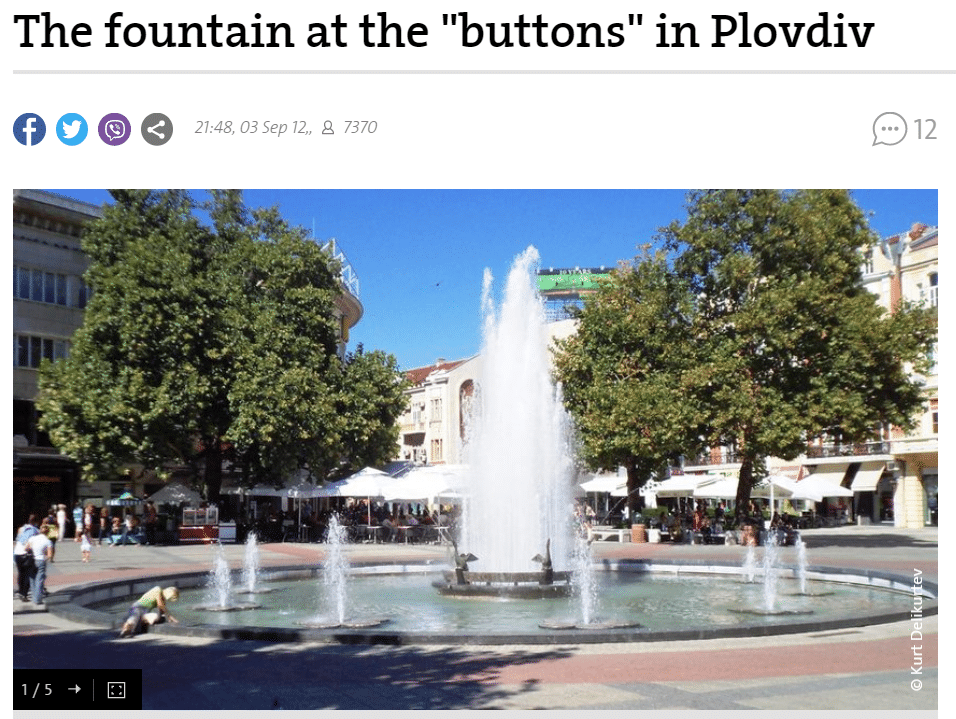
Flag is gsCTF{plovdiv}
Wheels Wheels Wheels (50)
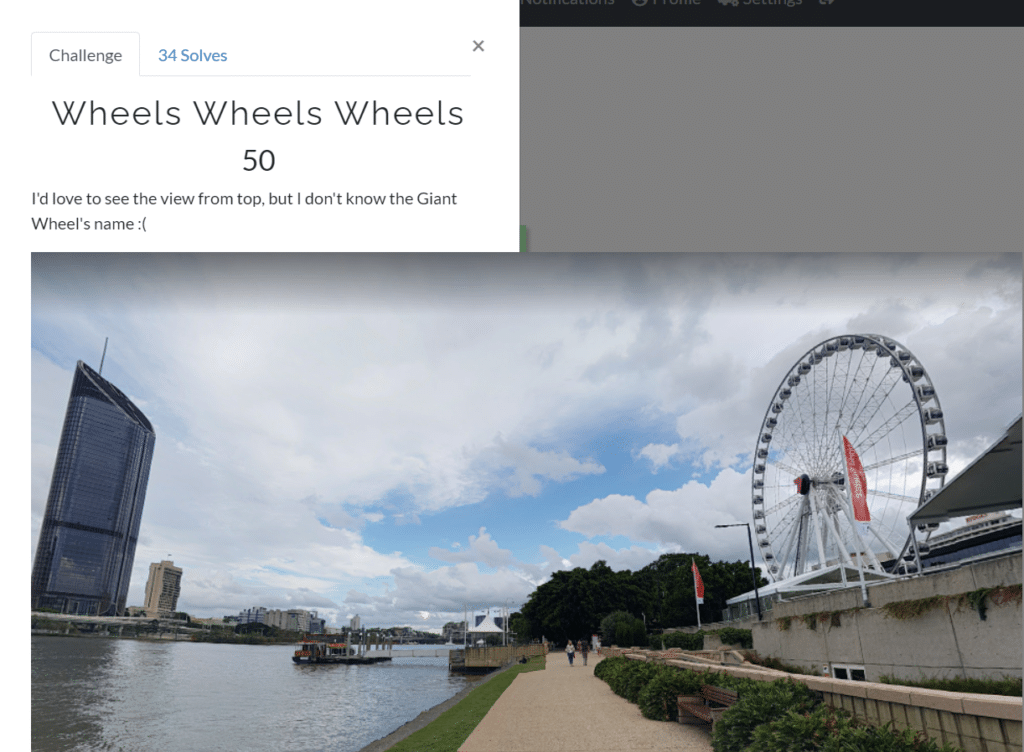
Like Where Am I Challenge I started looking for reverse searches on google but this time sadly no result then I just got the idea to crop the picture. So I cropped the giant wheel and reverse searched for the building and Voila!! This time I was successful in finding the flag
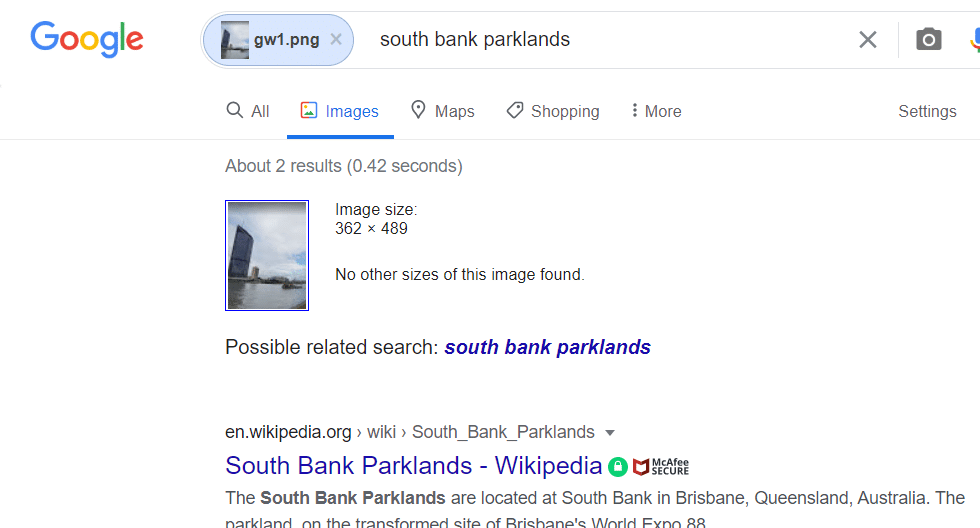
As in the description, it says I have to give the name of the Ferris wheel as the flag, so I searched the Ferris wheel in Parklands and got the answer it was The Wheel of Brisbane. So the flag is gsCTF{the_wheel_of_brisbane}.
Cryptography Challenges
Et Tu, Brute (30)
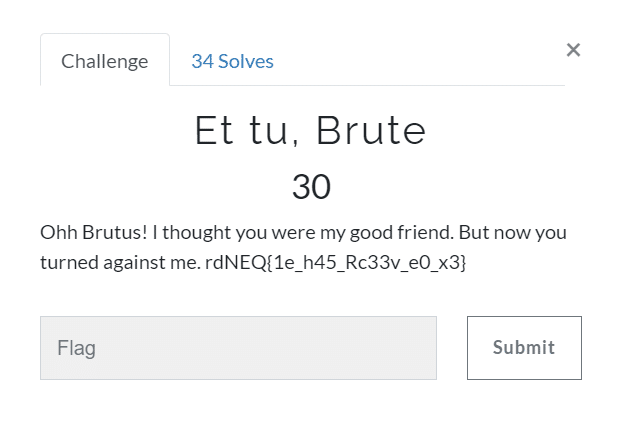
After gathering some experience in the CTFs, you will probably guess this easily as this is ROT encrypted and after spending some more time I found that it was ROT15 and the flag was gsCTF{1t_w45_Gr33k_t0_m3}.
Communication is the key (40)
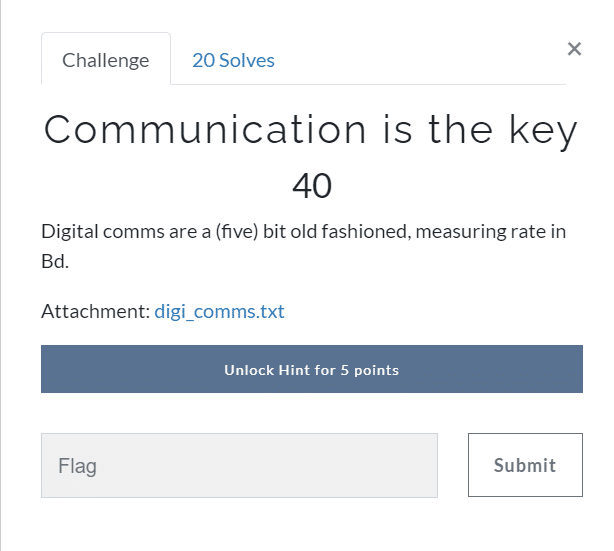
In this challenge, I got a text file consisting of binaries, and the description says that it is a five-bit measuring rate in Bd. So after crawling the google for five-bit ciphers, I found Baudot cipher which is not used now exactly as the description says. So we will decrypt it easily using the online decrypter from https://www.dcode.fr/baudot-code which is, in general, an excellent website for solving crypto challenges.
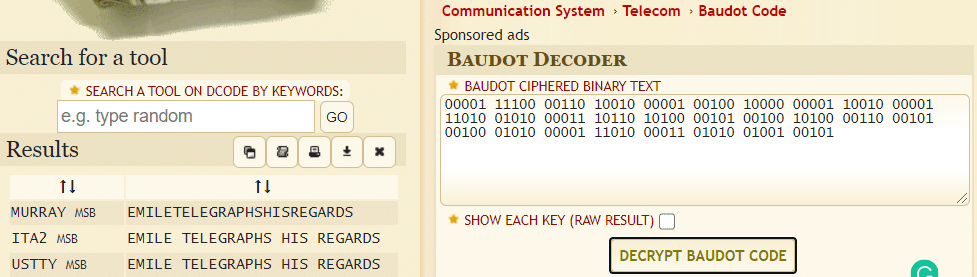
And from here it was just easy I have to put the flag in the CTF format, i.e. gsCTF{EMILE_TELEGRAPHS_HIS_REGARDS}
Oh so French! (50)
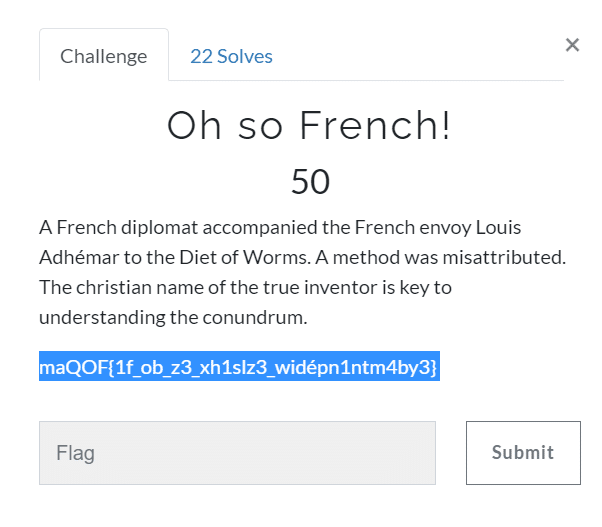
If you read the description carefully and search French cipher on google, you will quickly know that Vignere Cipher will be used here, but that is where the challenge begins as to decode vignere cipher we need a key as told in the challenge that we should get the Christian(First) name of the actual inventor might be the key. After some crawling, I found the name of the actual inventor was Giovan Battista Bellaso so that the first name might be the key and Voila!! My guess was correct, and I found the flag.
gsCTF{1s_it_l3_ch1ffr3_indéch1ffr4bl3}
The Game of Base (60)
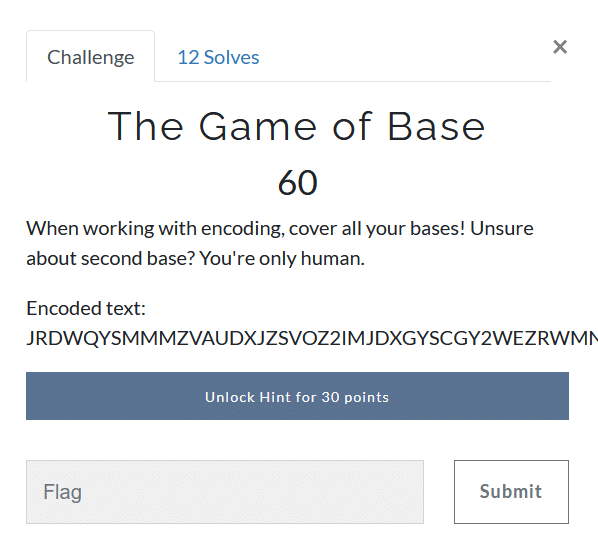
Looking at the challenge description and name, we can figure out that this challenge involves decoding multiple Base Encodings (Base64, Base26, etc.)
Luckily there is a simple tool basecrack by mufeedvh on Github for this purpose. Quickly cloning the repository and running the script decodes the string.
The flag is gsCTF{y0u_sc0r3d_4_h0m3_run}
Reverse Challenges
Level 1 (30)
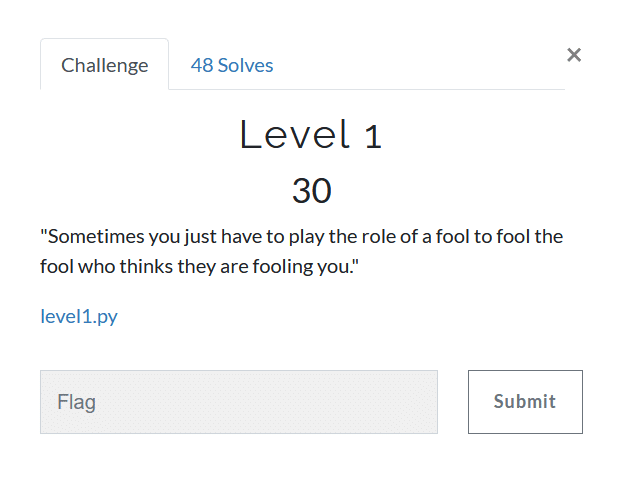
Running the given python file we get a string in flag format: gsCTF{y0u_G07_f0013d_w17h_Th15_f14g. lol XD}.
Hmm, this doesn’t really look like the flag so we open the file in a text editor and there it is, the real flag in the comments.
gsCTF{tH1s_i5_4_r3aL_fL4g_y0u_Mu5t_sUbm1T_1t!}
Level 2 (40)
This time on running the script, it’s asking for the password. Looking at the source code we see that there is a simple string compare function which has the correct flag.
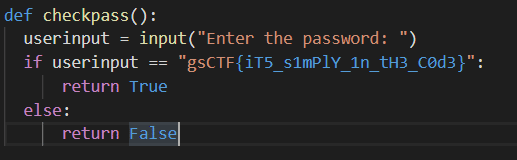
Flag: gsCTF{iT5_s1mPlY_1n_tH3_C0d3}‘
Level 3 (50)
We proceed as in level and look at the source code. This time we see that the string is simply cut in parts.
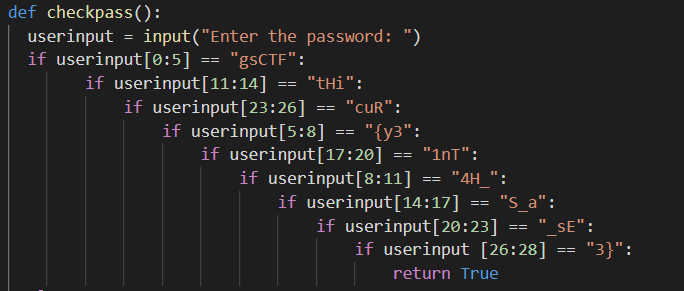
On rearranging the string, we find that the flag is: gsCTF{y34H_tHiS_a1nT_sEcuR3}
Level 4 (60)
Repeating again and opening the source, we see that the password is first encoded by a function woah() with a key, encoded in UTF-8, and then encoded with base64. The final string is compared to a given value. So reversing the string will get us the flag.
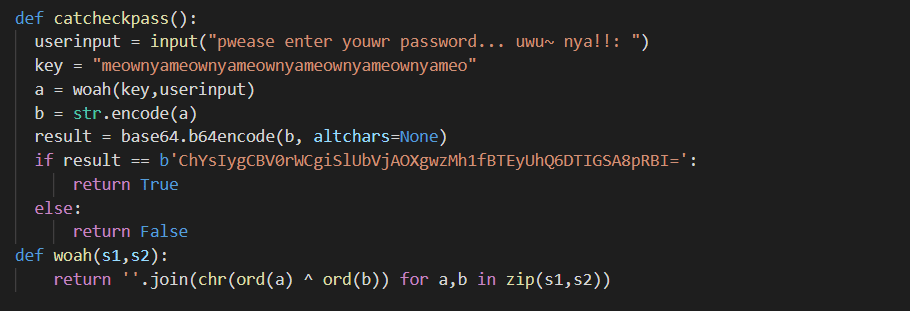
We first decode the string with Base64 and we get some ASCII values.
,#(]+X("JUV0^
32
_12R:
2H)D
We see that woah() is just XORing the string with a given key. So simply passing the decoded string in woah will give us the flag, and here it is: gsCTF{d0N7_L34v3_y0uR_x0r_K3y_bEh1nD!}
It sounds fishy! (40)
Opening the given malicious.exe file in a virtual machine (to be safe) shows that the file is corrupted. But simply running the file command on Linux tells us that it is a pdf file.
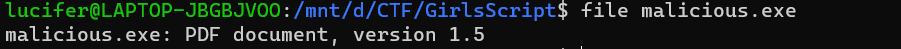
On renaming and opening the file in pdf viewer, we notice that there is white text on white background. Simply copying all text and pasting on a notepad gives us the flag which is: gsCTF{1_Th0uGh7_y0u_w0u1dn7_Se3_m3!}
Get the latest tech news and updates, ethical hacking tutorials, and cybersecurity tips and tricks. Check out MeuSec for more.
Sometimes we include links to online retail stores and/or online campaigns. If you click on one and make a purchase we may receive a small commission.


Comments: